In today’s cloud-driven landscape, containerized workloads are at the heart of modern applications, driving agility, scalability, and innovation. However, as these workloads become increasingly distributed across multi-cluster, multi-cloud, and hybrid environments, the challenge of securing them grows exponentially. Traditional network security measures designed for static network boundaries are ill-suited for the dynamic nature of containerized applications.
The Challenge: Protecting Cloud-Native Workloads
The rapid migration to the cloud has resulted in an explosion of cloud workloads, ranging from traditional applications with minimal cloud adaptation to cloud-native applications exploiting the cloud’s elasticity and scalability.
Cloud-native applications, in particular, rely on microservices architectures, ephemeral and highly elastic containers, and CI/CD automation through platforms like Kubernetes. These applications embrace the cloud’s dynamic nature but introduce unique security challenges. Unlike traditional workloads, cloud-native applications lack fixed network boundaries and are highly distributed across hybrid and multi-cloud environments. They demand a new approach to network security.
The Need for a Container Firewall in DevOps Flows:
The essence of DevOps is speed and automation. Containers and orchestration platforms like Kubernetes enable rapid software development and deployment. However, this agility brings heightened security concerns.
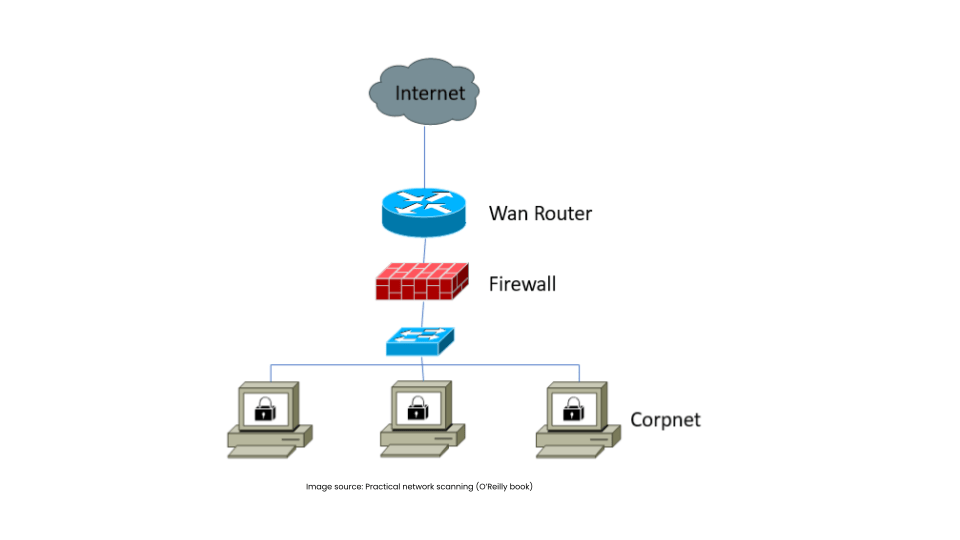
Traditional firewalls, rooted in perimeter defenses, struggle to secure dynamic containerized environments effectively.
Fig 1: Legacy firewall topology
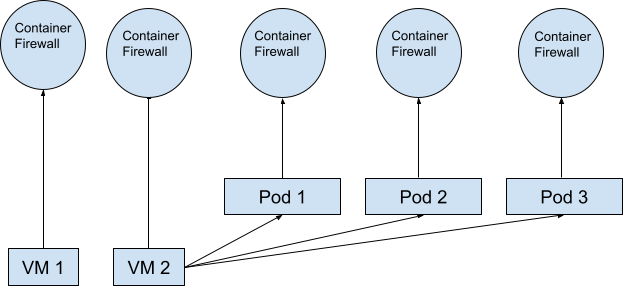
A new approach is essential to meet the security needs of modern DevOps. A container firewall that seamlessly integrates into the DevOps workflow, is configured as code and achieves uniform enforcement is critical.
Fig 2: Container firewall topology
Calico Container Firewall fulfills this need by automating security, ensuring consistency, and tightly aligning security with development practices.
Calico Container Firewall: Doing Container Network Security the right way
Calico’s container firewall addresses the evolving security needs of cloud-native workloads. Deployed as code, this innovative solution offers deep visibility, granular security controls, intrusion detection and prevention, and application layer (L7) protection. It empowers DevOps and platform teams to secure their containerized workloads effortlessly.
Key Features
Full traffic visibility
Get complete network topology and traffic visibility with a graph-based visualization of your Kubernetes deployments. Troubleshoot security and compliance gaps, connectivity breakdowns, anomalous behavior, and security policy violations.
Secure outbound traffic
Deploy granular, zero-trust workload access controls from individual pods in Kubernetes clusters to external resources, including databases, internal applications, 3rd-party cloud APIs, and SaaS applications. Secure pods using fine-grained DNS egress policies and NetworkSets.
Microsegmentation
Secure lateral communication between pods, namespaces, and services. Achieve workload isolation based on environments, application tiers, compliance needs, user access, and individual workload requirements. Get automatic and continuous policy recommendations for namespace-based isolation.
Egress gateway
Enable existing network security solutions, such as firewalls and gateways, to enforce traffic policies on outbound traffic from specific Kubernetes workloads. Calico Egress gateway assigns a fixed IP address to traffic leaving from designated workloads, enabling existing network security controls to enforce security on outbound traffic from Kubernetes clusters.
Intrusion detection and prevention
Protect against data exfiltration and malware attacks by blocking communication to known malicious IPs, domains, and VPNs. Integrate open source and 3rd party threat feeds to ingest the latest threat intelligence data for use in security policies.
Protection from DDoS attacks
Prevent and mitigate DDoS attacks with host and application level security policies.
Network-based anomaly detection to detect zero-day attacks
Stop zero-day attacks with heuristics-based learning of anomalous network activity. Detect Indicators of Attack (IoA) from network flow logs, DNS, and HTTP logs.
Honeypod and deep packet inspection
Detect suspicious activity using decoys disguised as a sensitive asset (called honeypods) at different locations in your Kubernetes cluster. Combine with deep packet inspection to identify source and method of attack.
Web application firewall
Protect against HTTP-based attacks such as OWASP Top Ten and other non-conforming HTTP headers, especially for lateral communication in a single container-centric firewall.
Security policy management
Collaboratively author, stage, preview, enforce and manage security policies with Calico’s unified policy framework. Test policy before deployment using staged policies. Deploy policies in hierarchical policy tiers based on roles and permissions to ensure consistent enforcement of policies. The manager UI has a policy board so teams can easily view and manage all active and inactive security policies in the Kubernetes cluster.
Automate deployment with security as code
Specify security and observability as code (SOaC). SOaC uses Kubernetes primitives and declarative models to deploy network security ensuring identical security and observability for all workloads across multi-cluster environments.
Multi-cluster and cluster mesh enforcement
Single pane of glass to manage and enforce consistent network security across multi-cluster and cluster mesh environments.
Architecture and Deployment
With an easy and simple operator-based installation, Calico can be deployed on any cloud – private or public supporting most commonly used managed and self-managed Kubernetes services. The Calico container firewall is deployed as a daemonset, making it highly scalable, distributed and dynamic. DevOps users can also utilize the Helm installation for managing Calico deployment.
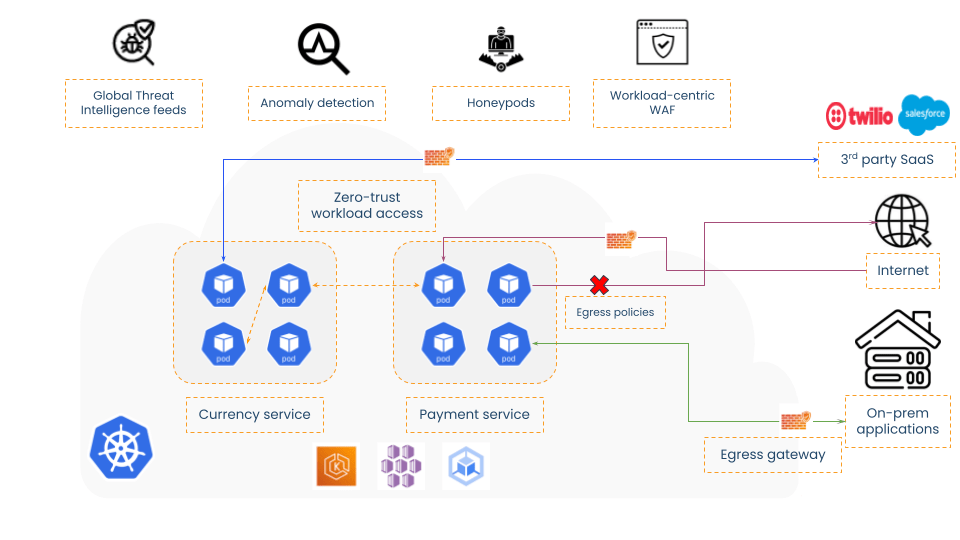
Due to the distributed nature of microservices and substantial increase in east-west traffic, the container firewalls need to be able to prevent lateral movement of threats. The Calico container firewall, unlike a traditional firewall, is deployed alongside the workload. This makes it best suited for protecting both north-south and east-west traffic in cloud-native applications.
Fig3: Calico Container Firewall
Use Cases
Calico container firewall addresses some of the most common network security use cases for containerized workloads.
- Prevent Data Exfiltration – Calico Container Firewall prevents unauthorized data exfiltration, securing sensitive data within trusted environments.
- Protect Against Known and Zero-Day Network-Based Attacks – This solution safeguards workloads against known and zero-day network-based attacks, using threat intelligence feeds for proactive protection.
- Prevent Lateral Movement of Threats – Implement microsegmentation to secure lateral communication between pods, namespaces, and services, preventing threats from spreading within the network.
- Enforce Zero-Trust Network Security – Fine-grained access controls enforce a zero-trust security model, requiring thorough authentication and authorization for every network connection.
- Secure Container Workloads with Existing Network Security Tools – Seamlessly integrate Calico Container Firewall with existing network security controls, such as firewalls and gateways, for enhanced overall network security.
Benefits:
- Multi-Cluster and Cluster Mesh Enforcement – Achieve consistent network security enforcement across multi-cluster and cluster mesh deployments, simplifying complex security challenges.
- Seamless Integration with CI/CD Pipelines – Deploy security as code (SOaC) within your CI/CD pipeline, automating security policies throughout development and deployment for reliability and consistency.
- Outbound Traffic Protection – Ensure security on outbound traffic, preventing data exfiltration, malware, and other threats by enforcing security controls.
- Threat Detection and Prevention – Proactively identify and block attacks from known and unknown attackers using threat intelligence feeds.
- Integration with Existing Network Security Controls – Combine the strengths of existing network security solutions with Calico Container Firewall, enhancing overall security for containerized workloads.
Conclusion
Calico Container Firewall offers a comprehensive solution for securing containerized workloads across dynamic, distributed environments. DevOps and platform teams can embrace cloud-native innovation while ensuring robust network security. Welcome to the future of container security with Calico’s container-centric firewall.
Book a demo to see Calico Container Firewall in action.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!